Cyber Security Protections, System Consultancy, Secure Networking Helpdesk Support for Business
The Australian Government Standard in Cyber Protections
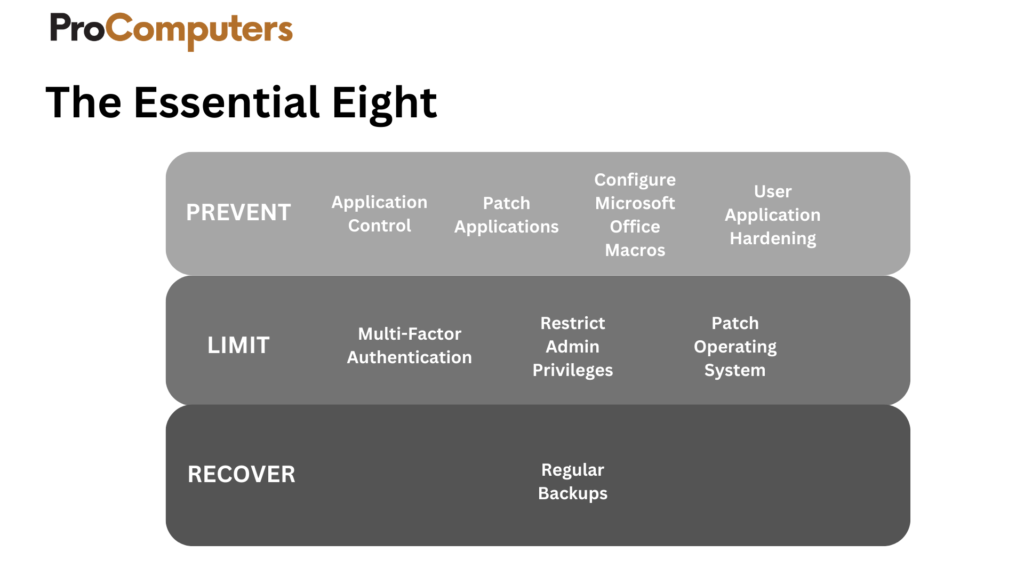
Essential Eight
The Essential Eight is a comprehensive cybersecurity framework from the Australian Cyber Security Centre (The Australian Government), comprising eight mitigation strategies. These include measures like application whitelisting, patching, user application hardening, and multi-factor authentication. By implementing these strategies, businesses can significantly reduce the risk of cyber threats, fortifying their resilience, safeguarding sensitive information, and maintaining operational continuity. This guide is crucial for proactively managing and mitigating cybersecurity risks in today’s dynamic business environment.
The Pro Comptuers Difference
Strength through adding security layers
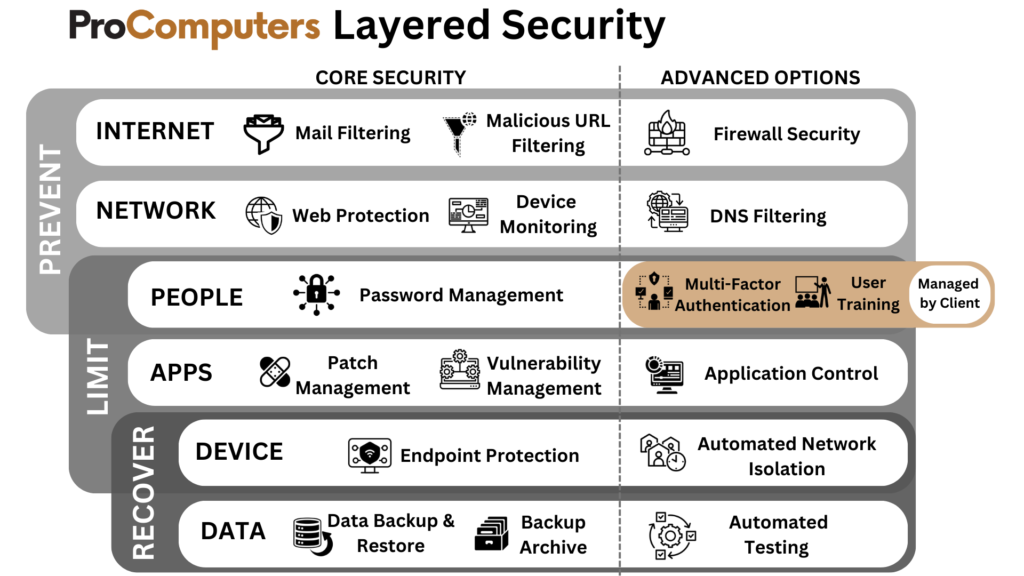
Layered Security
Layered Security stands out as superior to the Essential Eight due to its holistic and diversified approach to cybersecurity. By deploying a multitude of defence measures across various levels of an organisation’s IT infrastructure, Layered Security creates a robust and intricate defence system. This comprehensive strategy incorporates tools like application defence, application patching, e-mail filtering, password management systems, multi-factor authentication, operating system patching, endpoint detection & response, frequent backups that are validated, and continuous monitoring of the environment to detect and respond to attacks, forming a complex set of layers of defences that makes it challenging for attackers to breach all layers.
Prevent Attacks
Application defence
Application defence, an integral part of the cybersecurity arsenal, complements the Essential Eight by focusing on safeguarding specific applications. It provides targeted protection against vulnerabilities and exploits, enhancing the overall resilience of an organisation’s software ecosystem.
Patch Applications
Email Filtering
A vital frontline defence, email filtering plays a pivotal role in preventing phishing attacks and malware distribution. By filtering out malicious content, organisations can bolster their defences against threats that may otherwise exploit human error.
Endpoint Detection & Response
Building on the Essential Eight’s principle of endpoint protection, Endpoint Detection & Response (EDR) actively monitors and responds to suspicious activities on individual devices. This is a next generation service from the traditional antivirus products. It improves upon the traditional products by monitoring the behaviours your machines, keeping track of the changes that are made in your system and arresting the process or service, you can roll back your system to prior to the attack in most cases. This enhances the organisation’s ability to detect, neutralise and remediate potential threats swiftly.
Monitoring Events
Complementing the Essential Eight’s focus on continuous monitoring, this feature ensures vigilant oversight of network activities. Monitoring events in real-time allows for early detection of potential security incidents, enabling rapid response and mitigation.
Limiting the Extent of Attacks
Enhancing user access security.
A Password Management System aligns with the Essential Eight’s multi-pronged approach. It strengthens the organisation’s defence by enforcing robust password policies and minimising the risk of unauthorised access.

Critical for closing security loopholes.
Augmenting the Essential Eight’s emphasis on OS patching, this feature specifically targets vulnerabilities in the operating system.
Regular patches are critical for closing security loopholes and maintaining the overall integrity of the system.

Prevent attacks + limit exposure

Recover data + system availability

A key component in limiting the extent of attacks.

Enabling a swift and targeted response.
This feature extends the Essential Eight’s endpoint protection by adding a response mechanism. In the face of an attack, it enables a swift and targeted response to contain and mitigate the impact on individual devices.

Neutralise cyber threats promptly.
Aligned with the Essential Eight’s proactive approach, this feature emphasises a structured and effective response strategy. It ensures organisations are well-prepared to handle and neutralise cyber threats promptly.
Email compromise
Business Email Compromise
(BEC) fraud - where a financial loss was recorded
Online banking fraud
Recover Data & Systems Availability
Multiple Daily Backups

An extra layer of data preservation.
In line with the Essential Eight’s recommendation for secure backups, the backup archive feature adds an extra layer of data preservation. It facilitates organised storage and retrieval of historical data, ensuring comprehensive recovery options. Archiving for up to 7 years is possible for all files, folders, databases and Microsoft 365

Effective when needed the most.
Strengthening the Essential Eight’s call for reliable backups, this feature ensures the ongoing validity and reliability of backup data. Regular validation checks guarantee that backup systems are ready to restore data effectively when needed the most.

Cyber Self-Assessment tool
The Australian Government’s Cyber Security Assessment Tool empowers businesses and individuals to enhance digital defences. Accessible through the provided link, this tool offers a comprehensive evaluation of cybersecurity practices, identifying vulnerabilities in network security, data protection, access controls, and incident response planning. Gain insights to strengthen cybersecurity posture and align with the government’s commitment to a secure digital environment. Explore the tool for resilience.
Pro Computer offers no-cost support in understanding and completing the assessment—contact us today to arrange.
You've worked too hard in business to not protect it properly
Don’t wonder if, let us help you find out and get your business secure.
The Pro Computers team can help you understand, implement, and assist you with managing the Essential Eight Strategies in your business. Contact Pro Computers today for a No obligation, Free onsite discussion to help you get started.
Phone Plans
Business
Pro Computers makes Business IT Simple.
Pro Business
Catering to our esteemed business clientele, Pro Computers are committed to delivering customised solutions emphasising advanced computer security and rapid speeds, fostering a secure and efficient digital landscape for your professional endeavours.
The Pro Computers Difference.
Pro Computers is your trusted computer repair and IT services supplier.

Local Service
Experience top-notch technology solutions with our computer shops’ dedicated local service, tailored to meet your every need.

Unmatched Support
We pride ourselves on providing unmatched support to ensure seamless technology experiences for all customers.

Solutions for Everyone
Discover a wide range of tech solutions for everyone, catering to all computer needs for home or business.
Let Pro Computers help your business.
- Microsoft 365 Consultancy (including best practices for security)
- Secure Corporate Networks.
- Hotel Wireless Solutions and Support
- Helpdesk Support
- Business Machine Sales and Service